Do More
on WhatsApp
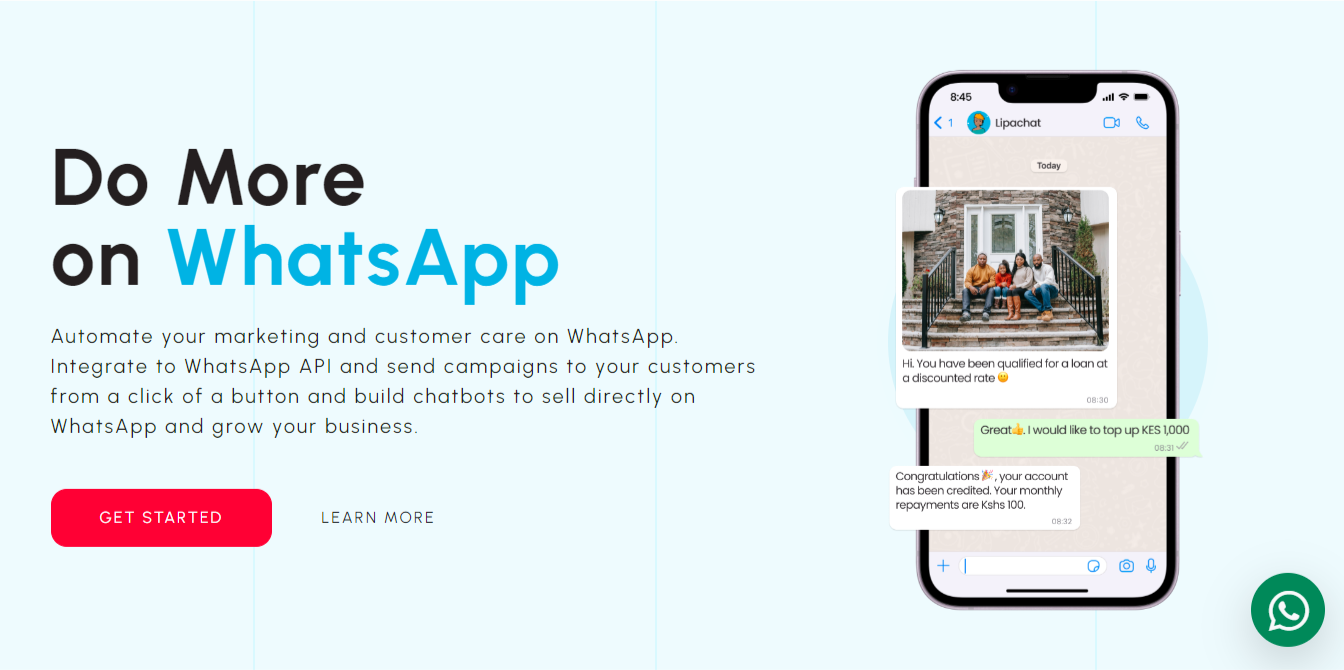
Automate your marketing and customer care on WhatsApp. Integrate to WhatsApp API and send campaigns to your customers from a click of a button and build chatbots to sell directly on WhatsApp and grow your business.
What We Do
WhatsApp API
Use our platform to connect your number to WhatsApp API and build business solutions directly on WhatsApp API with ease. Our sandbox allows building and testing multiple projects with robust analytics.
WhatsApp Chatbot
We develops chatbot solutions through which your businesses can automate sales, customer care and transactions on WhatsApp. Extend your product and service reach by plugging into Whatsapp’s vast user base.

Why you need WhatsApp API for Business
WhatsApp is the number one messaging platform in the world with global reach and over 1.6 billion users. By using WhatsApp API for business, a company can improve their customer satisfaction, loyalty, and retention, as well as increase their sales and revenue.
No text and media limitations like SMS
Send all types of media and text without worrying about character count
No more saving numbers on phone 1 by 1
Import them from excel
Forget about cumbersome broadcast lists
You can to thousands of contacts at a time
No more losing leads
Re-engage them through WhatsApp campaigns








